By Richard Enderby, Cyber Security Practice Lead
| Companies must continually review their approach to securing their cloud environments given how quickly the environment changes and threats evolve. This is where a Zero Trust way of thinking becomes crucial – one that trusts no user, device, or system whether it is inside or outside the cloud infrastructure. |
According to the Check Point Cyber Security Report 2020, cybercrime will cost the world $6 trillion annually by 2021. And with many organisations embracing the concept of remote working due to the COVID-19 pandemic, more devices than ever will try to access company data and systems stored in the cloud. With the security perimeter of the business no longer confined to the walls of an office building, traditional anti-virus and firewall solutions no longer provide adequate protection.
Today, valuable business data transfers continuously between software-as-a-service (SaaS) applications, infrastructure-as-a-service, data centres, remote users, Internet of Things devices, mobile phones, tablets, and more. All this contributes to providing cyber criminals with a wider attack surface than before.
So, how can the Zero Trust model be applied to a cloud-centric organisation reliant on employees accessing vital information irrespective of their physical location or the device used?
Combining forces
|
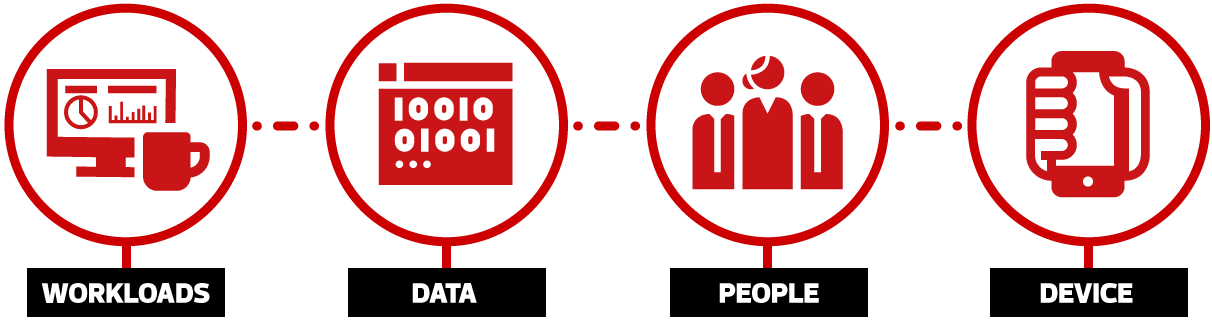
By incorporating four critical elements – workloads; data; people; and devices – the Zero Trust approach to the cloud is far-reaching. It revolutionises how companies ensure the safety of their most vital asset – their data. |
 |
Securing workloads, particularly those running in the public cloud, is essential since these cloud assets are vulnerable and attractive targets to malicious actors. Just consider the business impact a compromise on a virtual machine or container could have on business continuity. | |
 |
Protecting data while it is shared continuously between workstations, mobile devices, application servers, databases, SaaS applications, and across the corporate and public networks, is one of the cornerstones of the Zero Trust model. | |
 |
And to do so effectively, attention must turn to people. Most data breaches involve stolen credentials. So, the traditional username and password methodology of proving the identity of a user needs to be replaced by something more innovative. Identities are easily compromised, so access control to the data must be strengthened. | |
 |
Finally, every device that connects to the corporate network should be treated as a threat vector, whether it is a workstation, a mobile phone, or an IoT device. Security teams must be able to secure every device on their network and isolate it if compromised irrespective of its geographic location. |
Centralising security
Going the Zero Trust route provides the business with better visibility of its data, infrastructure, and risks faced. In doing so, management will be able to identify where the likely weak points are. By using effective cybersecurity solutions, this can be done proactively and defend the organisation against both known and unknown threats.
Part of this involves a centralised security management approach that significantly improves operational efficiency. Having sight of all cloud touch points behind a single pane of glass empowers technical teams to make more informed decisions on cybersecurity implementations. It also results in a single, unified policy that considers users, devices, workloads, the cloud, and gateways.
Ultimately, Zero Trust brings with it real-time threat intelligence to help combat cyber attacks more effectively and with as little disruption as possible to existing business processes.

To read more about this topic in our Cyber Security Guide click here
To find out more click here


