In this series, I want to share my holistic view of cybersecurity, not just as a series of technologies, but a business strategy.
'Security Transformation' is a move away from 'doing cybersecurity' to 'doing business securely'.
Put simply, I want organisations to move away from perceiving security as being an IT function - where it has limited impact with regards to business process - to one that allows all parts of the business to work securely.
Part 1: https://news.uk.cdw.com/cybersecurity-security-transformation
Part 2: https://news.uk.cdw.com/security-transformation-quality-approach
Part 3: https://news.uk.cdw.com/security-strategy
The security status quo
In this article I would like to present the concept of what we’re calling “Security Transformation” at CDW.
But to do so, it’s important to first look at the status quo and why transformation may be required.
There’s something funny about information security today: it’s heavily focused on technology. In fact, it’s almost exclusively focused on technology. And yet security, fundamentally, has nothing to do with technology.
Over my 25-year career in security - during which I’ve been everything from a teenage hacker, government operative, technical consultant, CISO, speaker, lecturer, and author - I’ve come to realise that strategy and business focus are far more important than technology when it comes to protecting our organisations. Don’t get me wrong, technology helps, but it is not the silver bullet.
This is the core reason that, despite my title of ‘Chief Technologist’ at CDW, I consider myself primarily a strategist.
During the process of joining CDW, I was asked what I would consider a typical question for a security role, whether as a practitioner or in a strategic sales capacity.
“What trends do you see now and in the future, and how should we adapt and/or capitalise?”
It’s a reasonable question. Like most other areas in IT, we constantly see new trends developing and being adopted with various levels of success. Security is no different.
However, despite what much of the market says, I feel it’s less relevant in security.
Why the security industry is less affected by technology trends
Firstly, compared to other areas of technology, different organisations are at vastly different stages of their security journey. The fundamentals must always come first, there is no point in implementing the latest and greatest security technologies without a solid foundation. They simply can’t be effective otherwise.
Secondly, security, as a general concept, is something that needs to be highly tailored to your organisation and its specific activities. Acquiring a litany of security technologies is not a security strategy, and the protection provided to your business and business processes by doing so is liable to be ineffective, or even lacking completely.
The bigger issue in the security industry: more breaches, more spending
But I feel we face a much larger issue still in our current approach within security. And it’s why my answer was that there are only two trends that concern me within information security, and they could even be considered one trend.
Every year we spend more money on information security. With spending increasing both in absolute terms and as a percentage of IT and business spend.
And every year things get worse.
We see more breaches, more records lost, more damage caused.
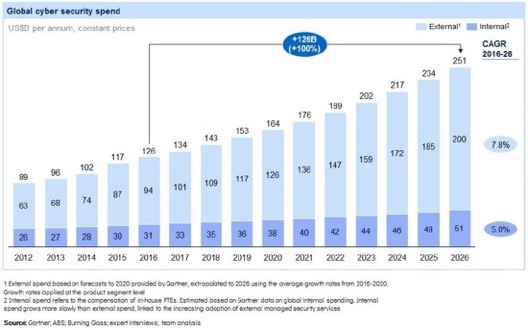
Source: Evolveetfs
Source: Medium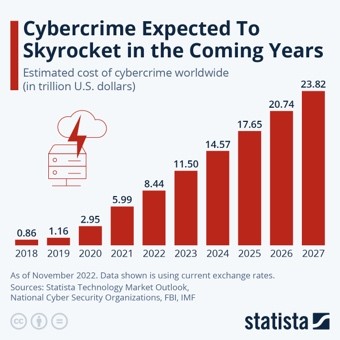
Source: Statista
At what point do we stop ‘doubling down’ on an approach that is not working and is not cost-sustainable, or at least cost-justifiable, even if it did work??
This question is especially pertinent when there is an alternative approach that has been time-tested in many other sectors: quality management.
Consider that security vulnerabilities are defects. Whether in code, configuration, build, architecture, process, even human behaviour, it is these defects that are exploited by attackers to do things that they shouldn’t have been able to do. That could be to gain access, disable systems, steal data, etc. Without these vulnerabilities, threat actors would be about as threatening as a badger to a rhinoceros, and security operations functions would have a lot less work to do.
How some industries get it right
In other industries such as manufacturing, oil and gas, aerospace/aviation, automotive, healthcare, etc., there is a strong focus on eliminating the root causes of incidents so that they do not occur, or reoccur.
Unlike much of the information security sector, these industries don’t leave the processes (or lack of processes) ultimately responsible for creating the incidents in place; they address them as a priority. Not following this approach means that we, in security, are not only less effective, but incur never-ending costs, and produce no cumulative improvement.
Instead, they focus most of their resource on mitigating and responding to the resulting risks and incidents.
Every finding is used to track down a root cause, which is then typically addressed. Defects from a particular addressed root cause stop and do not reoccur. As they address more and more root causes, the number of defects, risks, and incidents decreases cumulatively over time.
And that is why the rates of issues and incidents in those industries trend downwards over time as shown below and do so with fixed or decreasing spending.
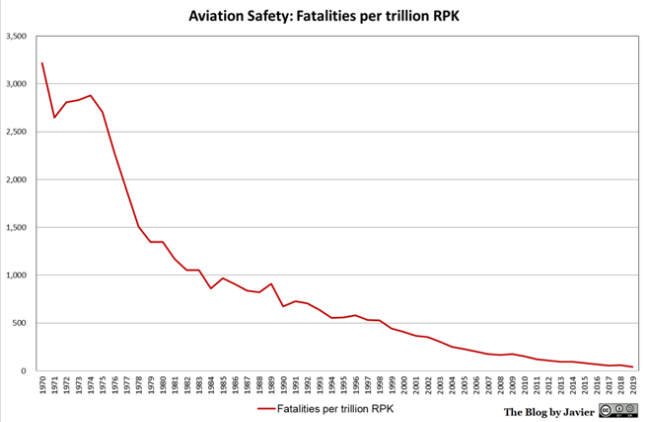
Source: The Blog By Javier
This is in stark contrast to the trends we saw earlier in information security, where the current approach focuses mostly on managing symptoms; meaning spend and issues only increase over time.
That, in a nutshell, defines the difficulties with our current approach and the need for change.
So, how do we define ‘Security Transformation’?
The aforementioned difficulties in the security field and need for change are why we came up with the concept of Security Transformation, which we define as follows:
The transition away from a siloed ecosystem of security technologies meant to mitigate threats to organisations’ ever-increasing vulnerabilities, and towards an approach where organisations define business and IT processes to be more fundamentally secure.
This approach means the business has fewer and fewer vulnerabilities [over time] in the first place, reducing the need to ramp up security capacity [and cost], which cannot scale effectively.
Or in other words, a shift away from “doing cybersecurity” as we do today, and towards “doing business securely” instead.
It involves a fundamental change; moving security from being an IT function where it has limited impact with regards to business process, to one that allows all parts of the business to work securely.
In many ways, this produces benefits usually associated with Enterprise Service Management (as my fellow Chief Technologist for Digital Enablement, Jaro Tomik, will tell you); bringing together business units and processes to create synergies and quality improvements throughout.
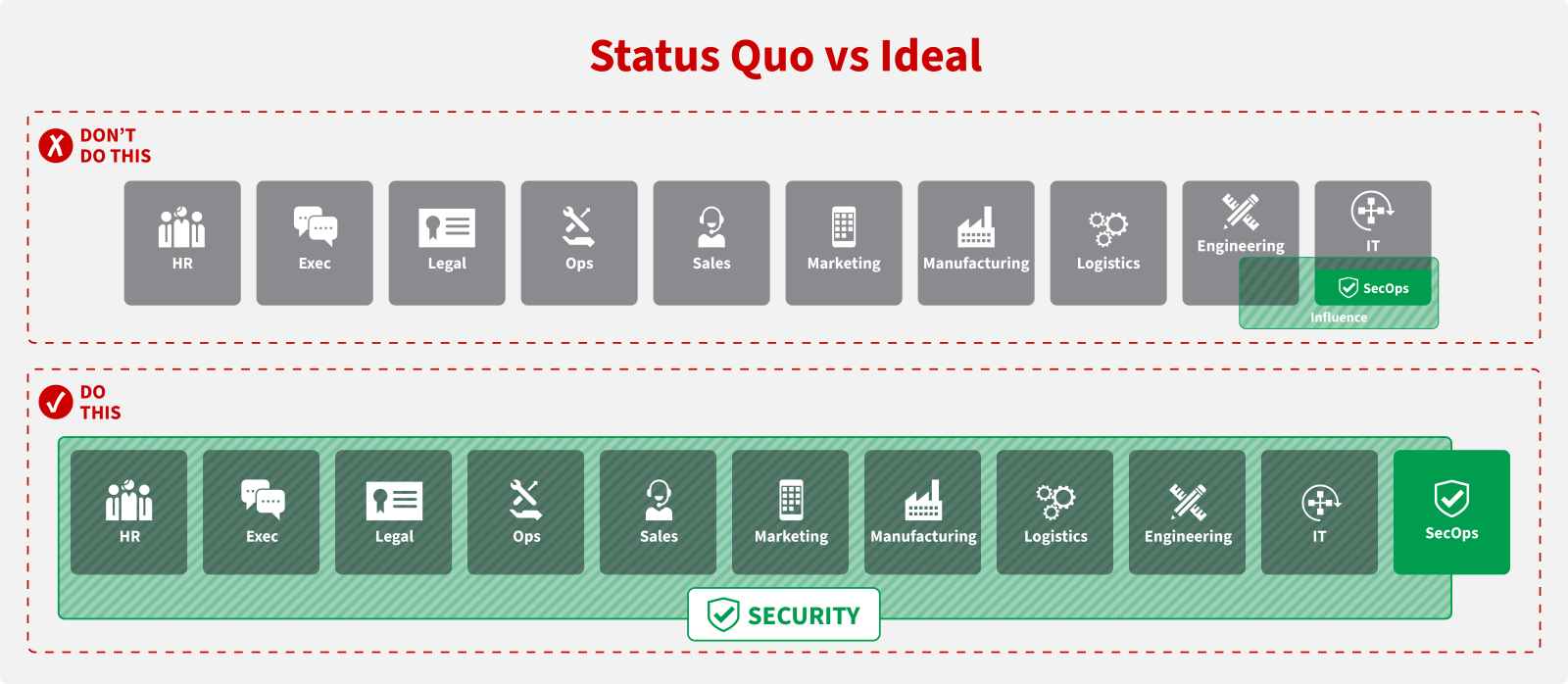
It’s a recipe for long-term improvements, not just to your organisation’s security posture, but with numerous additional business benefits as well. This is all driven by making security a quality management function rather than purely a reactive [and often limited] risk-management one.
It’s the potential of driving this change to CDW’s customers that has brought me here, and it’s a journey we hope you’ll trust us with.
Join us for part 2 of this series where we’ll take a deeper dive into why a quality-led, business-centric approach to security makes more sense than an IT risk-based one. In parts 3 and 4 we’ll cover the importance of aligning security to business rather than technology, and how Security Transformation is implemented, respectively.

-2.png?width=1200&height=330&name=MicrosoftTeams-image%20(17)-2.png)