Cyber Resilience is a wide topic with a profound impact, and it’s impossible to cover it in its entirety, even in a three-part series like this. Here at CDW, we are looking to change the way organisations approach cyber defence, with a focus on withstanding the attacks as much as recovering from them after the incident (more on this later). Most would likely associate this topic with the security team. While security does play a large part, my belief is the bulk of the work and responsibility sits with the core IT operational teams. Looking at the CDW Hybrid Platforms Pillar, we have 10 focus areas; three of which, I would argue, fit perfectly into the conversation: Platform Security, Operations and Observability, and Data Protection/Information Management.
For this Hybrid Platforms Trends Series, I am going to focus on the following three topics:
- The Perception v reality of Cyber Resilience
- The importance of Data Observability
- Platform Recovery is not Business Recovery
The Perception v reality of Cyber Resilience
The first step in solving any problem is admitting there is one, a quote attributed to many people over the years but one that is still true in 2024. The way we approach the problem of Cyber today is not working, this much should be clear to anyone tracking the spend v incidents. We need to approach things differently if we are to work our way towards a day when cybercrime is on the back foot. Let’s look at the current landscape and how we can start to get back to basics and create a roadmap to that future.
The ever-increasing threat landscape
Ransomware-as-a-Service (RaaS) has opened new attack avenues to cybercriminals who lack technical expertise. Multi-cloud adoption and SaaS migrations have increased attack surfaces, which have been elongated to breaking point. Compounding the issue is the trend of not addressing technical debt and the potential points of compromise.
Many modern ransomware organisations operate like legitimate businesses, with their own organisational structure, support departments and employee benefits. This ‘big business’ approach increases the effectiveness of the attack and leaves security teams with a seemingly impossible mountain to climb.
This stretching of the technical landscape, combined with a need for innovation to remain market-relevant, and increased macroeconomic pressures, means that many organisations cannot focus on the root causes of cyber risk. We need to take a close look at the causes of these risks and overcome the perception versus the reality of Cyber Resilience.
Perception v Reality
When you talk about resilience, generally the topic turns to data protection, immutability, threat hunting, isolated recovery environments or a scare conversation about how being breached is inevitable. Seldom does it really talk about the two parts of the word’s meaning. Take a quick look at the Google Dictionary definition.
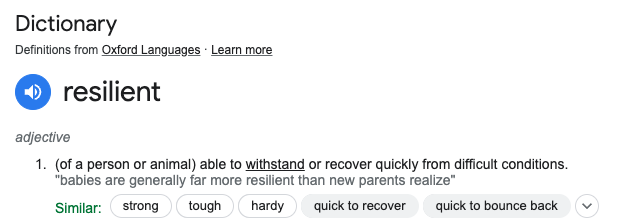
“Able to withstand or recover”, both these words are key, and we think that organisations need to focus as much on the ‘withstand’ as they do the ‘recover’ (or as we call it, survive). Let’s not be so scared of the threat that we focus all our effort on the survival of an attack, to the point we don’t address the root causes of the breach.
Changing Tactics of Cyber Criminals
One area of this conversation that drives our desire to change the approach is the impending evolution of the threat actors. One thing history shows us is that ransomware organisations are not against changing tactics as we evolve our defence strategies. In the past, the goal was to compromise and destroy; early malware would wipe out an organisation and itself - clearly not a money-making tactic!
Originally, with the 'mad hacker' approach, the goal was to compromise, encrypt and ask for money to access the keys. Now organised crime organisations are much more sophisticated (some even have help desks!), and we have noticed many small but important changes: attacking backups, compromising identity services, moving from mass encryption to just a few bytes per file (to avoid detection due to change rates) and multi-extortion tactics aim to compromise, exfiltrate data, then encrypt and ask for money.
The next phase of this could be to not even bother with the encryption element at all, just go for compromise, exfiltrate data, and then extort money. We are already seeing examples of this, with the people holding the data not only targeting the company, but also the family and non-work contacts of key decision-makers. The possible damage to corporate reputation, regulatory fines and now threats to family will be a much greater pressure than an encrypted system. Given we are getting good at providing recovery solutions now, downtime could be minimal from encryption.
The challenge is that backup, immutability, and isolated recovery environments won’t help protect against this next evolution in attack vectors. This is why we need to take the holistic approach and focus as much on the basics as anything else.
Getting back to basics
This change in attack vectors means we need to think about Cyber Resilience in a much more holistic way. No longer can it just be a security function, placing more and more technology into an organisation to try and mitigate underlying issues. The first stage of a more holistic approach is to make security a cross-organisation function and ensure everyone is responsible and bought-in, @greg talk about his ‘Status Quo v Ideal’ article.
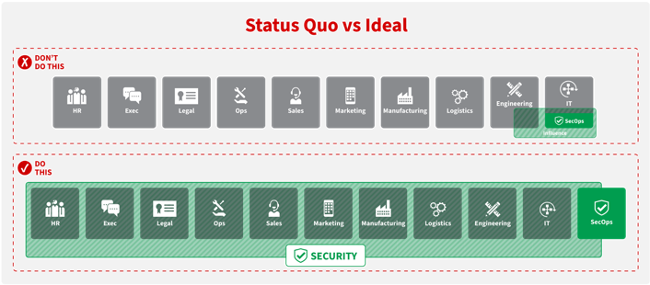
From my perspective, getting back to basics is a focus on core IT operations both at a platform level and as part of core software development. We need to address the root cause of attacks; this is a combination of technology and process. Here are ten good starting points:
- Improve visibility with holistic CMDB practices to ensure all assets are known.
- Utilise this CMDB data to consolidate inventory, reducing the number of possible attack points.
- Identity management should be front-of-mind, and both process and technology should be integrated.
- Address software and hardware procurement processes to ensure new solutions meet required standards, not just in business functionality but identity integration and vulnerability management.
- Replacement (or the upgrading) of outdated equipment and software to remove points of compromise, too many instances of old systems being placed on risk registers and left to become the next point of attack.
- Education; we need to adopt modern training practices that raise the technical literacy of all employees.
- Network Segmentation is a key line of defence, there is no reason the intern’s laptop should have access to critical backend systems.
- Development processes need to be updated to ensure code is being developed, stored and released securely. Too many instances of code compromise or make use of public code that includes vulnerabilities.
- Leverage automation to remove human error and ensure systems are deployed to a consistent secure standard (not more open RDP servers on the internet?)
- Patching; ensure a renewed focus is placed on managing existing vulnerability risks, if we manage the other points the goal is to reduce this effort over time.
While some processes, like Network Segmentation implementation, can be hard, they will make you understand every application, data flow and therefore the possible points of attack or compromise. Deployment is a journey, but one that would lead to a much more secure architecture and a greater understanding of all systems.
It is still worrying that many organisations don’t have these basic functions in place. Running at optimal effectiveness and asking for a CMDB output that can be considered accurate is often a huge ask. Without such a base level to start from everything else is going to be hard work.
Let’s get back to basics and address the root cause of breaches, rather than throwing more tooling to mask the issues!
Summary
With the cybercrime industry raking in $1.5 trillion USD in revenue annually, criminal groups and organisations are only gaining strength and growing in sophistication. We need to take a more holistic approach to Cyber Resilience; ensuring we can withstand as well as survive. This is the focus of our Cyber Resilience approach, helping you visualise your technology, people, and process landscape, allowing informed decisions needed to ensure you can withstand attacks. Finally ensuring you can survive when something slips through the gaps.

Join me in part two as we explore the topic of data observability in the context of Cyber Resilience

-3.png?width=1200&height=330&name=MicrosoftTeams-image%20(49)-3.png)