Welcome to Part 2 of the VMware SDDC series, in Part 1 we covered:
- Exploring the VMware Software-Defined Datacentre (SDDC)
- Early years of virtual networking
- 2012 and NSX was born
- Going beyond Layer 4!
- Help for the Operations team
To read Part 1 please click here.
In Part 2 we will cover the final elements of the NSX journey, with topics like:
- NSX-V to NSX-T
- The Quick Segue to SASE and SEE
- Other notable steps on the software-defined networking journey
- Developer-Ready
- How does all this innovation come together today?
- Future of Software-Defined Networking
Let's carry on the journey.
From NSX-V to NSX-T
As NSX took, off VMware had a challenge to consider: how coupled to ESX should NSX remain. and is VXLAN (the packet encapsulation used in NSX-V) the future?
Looking forward in 2017, it was likely obvious how the future of Cloud adoption would progress. A need to provide a networking solution that could span both on-premises and the hyperscale providers would become critical. The core challenge here was that NSX-V was tightly integrated into the vSphere ecosystem and would not accommodate non-ESX workloads, making it unsuited to cloud workloads.
This prompted the development of NSX-T (NSX Transformers) that would not be tied to the vSphere ecosystem. Starting life as early as 2016 and becoming mainstream in around 2020, NSX-T is now the de facto deployment mode for NSX.
The other big change was the move away from VXLAN to GENEVE (Generic Network Virtualisation Encapsulation) as the core packet encapsulation. This is the technology that allows NSX to deliver a Layer2 network segment over a routed network underlay. There are many reasons for the change, most around future-proofing the NSX stack and improving performance. If you would like to understand the full deep dive, this is a great place to start.
https://octo.vmware.com/geneve-vxlan-network-virtualization-encapsulations/
If you want to understand how all this virtual networking and encapsulation works in detail, this is a great starting point:
https://blogs.vmware.com/networkvirtualization/2017/09/nsx-t-routing-where-you-need-it.html/
Quick Segue to SASE and SSE
The VeloCloud acquisition in 2019 allowed the VMware networking story to evolve outside the data centre into the newly forming (at the time) Secure Access Service Edge (SASE) market and its evolution to Secure Service Edge (SSE). This is a technology that reaches much further than the core NSX use cases and a topic that I think would be best the subject of its own article. I think we should expect to see some evolution of this messaging at Explore, as the Edge become ever more important.
Other notable stops on the software-defined networking journey
Let’s look at a few of the other notable (good and bad) stop-offs on the VMware networking journey.
Do you remember AppDefense? No? Unsurprising as it never really took off. Announced at VMworld 2017 and retired in 2021, it had a short spell in the limelight as part of vSphere Platinum Edition. It was going to be the next leap in workload security, working at the process level inside the guest operating system to detect potential threats. Once detected it could trigger NSX DFW changes to isolate workloads and prevent lateral threat movement. Unfortunately, it did not take off, so headed over to the VMware software shelf.
Blue Lane Technologies is a blast from the past; acquired into the VMware family in 2008 it became the product we know as vShield. This was the technology behind hypervisor-level antivirus, another great technology innovation that has now evolved to be NSX guest introspection. Whilst not used as much for malware detection today, it is still the underlying technology for NSX IDS/IPS and Identity firewalls.
The DNE (Distributed Network Encryption) feature was deprecated in NSX-T 2.2, but for a short time offered some interesting capabilities, allowing for packet-level encryption between virtual machines. Maybe the technology was just a little ahead of its time!
vCloud AIR is another blast from the past; the cloud platform was sold to OVH in 2017. VMware did retain the HCX technology though, which today enables organisations to migrate workloads between cloud locations, especially for VMware on native cloud options like VMC on AWS or Azures AVS. The ability to stretch a Layer2 network from on-premises to the cloud and execute large-scale bulk VM migrations has enabled some rapid datacentre exits to take place over the years.
Developer-Ready
The virtual network capabilities we have been discussing also combine to provide the foundation for the VMware developer platform known as Tanzu. The acquisition of Pivotal in 2019 provided the base for Tanzu. Whilst this edition of the VMware article is not focused on Tanzu and VMware networking is not a requirement to leverage Tanzu, it is interesting to see how all these elements can combine to support and secure a modern application architecture.
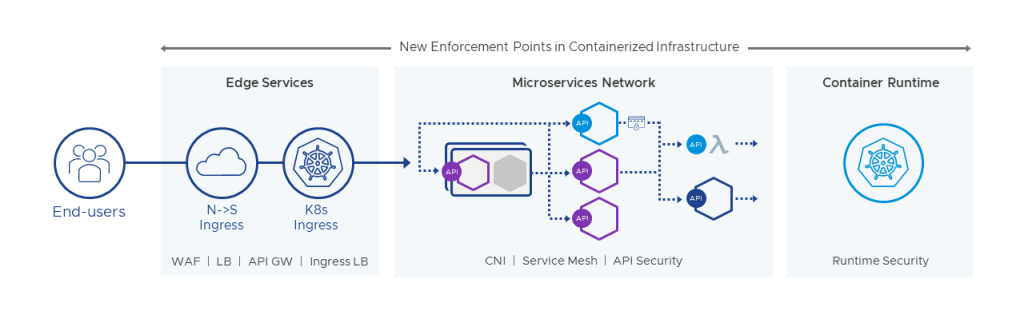
Software-Defined Networking supporting the modern application architecture.
How does all this innovation come together today?
The VMware networking portfolio has become the foundation for many of the stories and outcomes that VMware have been communicating over the past decade. From rethinking the network through to the foundation for private, developer-ready clouds, the NSX timeline below really captures the pace of innovation. The easiest way to think about software-defined networking is that it’s the operational model for networks that we all enjoy for virtual machines.
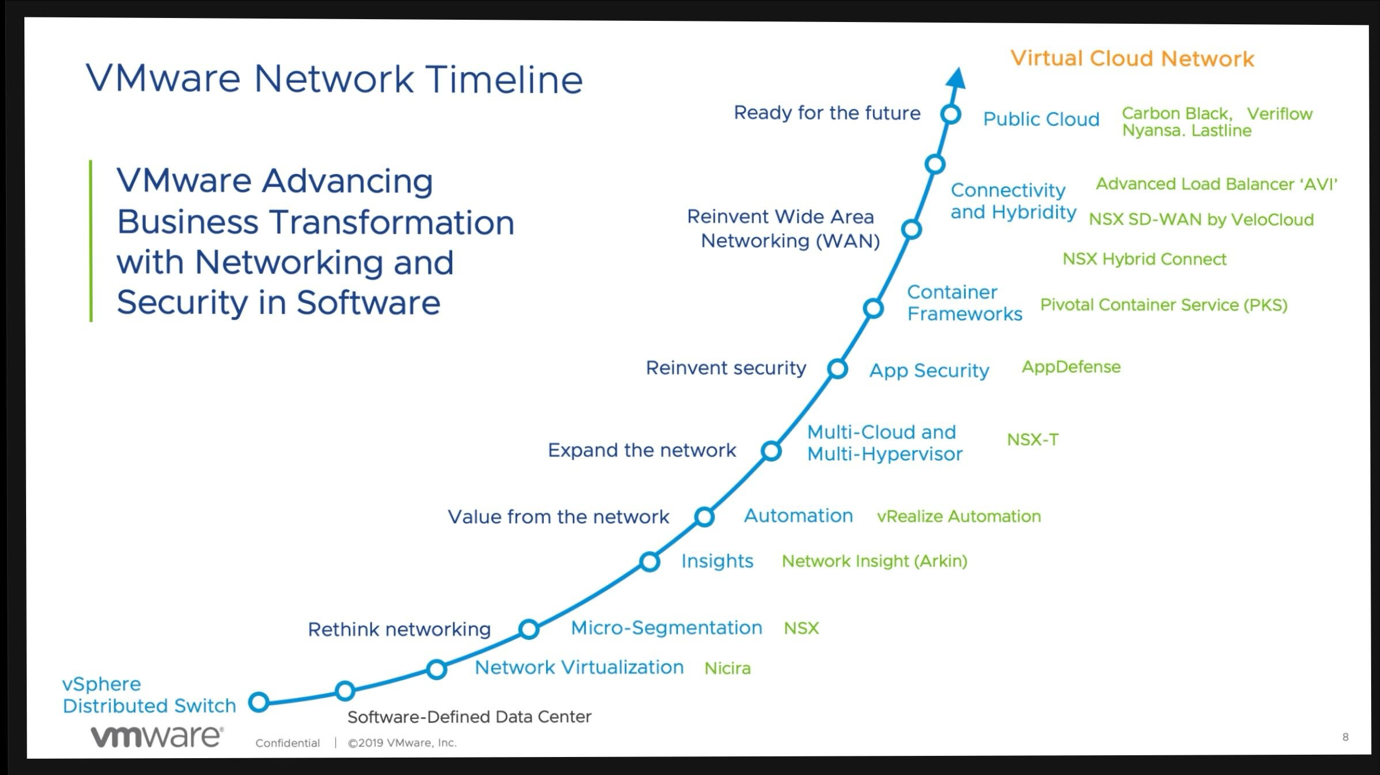
Today we have a software-defined networking solution that can provide a full range of features such as:
- Distributed routing
- Centralised firewalling
- Layer 2 Switching (over layer 3)
- Fully featured load balancing
- Site-to-site (SASE) and remote access VPNs.
- Distributed intrusiondDetection and intrusion protection
- Micro-segmentation
- Extend on-prem networking to the cloud for consistency
If we consider how these play out, as we build our private cloud environments, we get to realise some great outcomes.
- Improved security through segmentation from Layer 4 to Layer 7 with intrusion detection.
- Automated operations through the nature of software-defined and policy-driven principles.
- Technical debt consolidation as we reduce vendors (firewalls, switching, intrusion detection, secure services edge, and cloud orchestration).
- An underlying network to support modern application development and service mesh requirements.
I believe that software-defined networking is the foundation for building your hybrid cloud and should be on the roadmap for all organisations. We are seeing hybrid as the core operating model for many organisations over the next 5 years or more, and the network will be one of the key battlegrounds in realising the benefits and outcomes. Everything connected, all the time, as part of an automated ecosystem, is a core part of the CDW Platform of the Future vision.
Future of Software-Defined Networking
As we move into the future it will be interesting to see how the VMware networking portfolio continues to innovate and drive the industry forward. A few years ago, VMware released NSX Cloud and pushed into the world of native cloud networking. The message of a consistent policy that could be enforced by the technology native to the platform was ahead of its time. The idea is that you could set a policy on a workload and have NSX-T enforce it on-premises and Azure Network Security Groups (NSGs) do the enforcement in the public cloud. With the early announcements on NSX+ we can see VMware making a tentative return to this outcome. Is the market ready this time as we start to accept that hybrid cloud is the future?
Tackling the complexity and day 2 operations of a true hybrid cloud network needs to be the goal in the coming years. Providing end-to-end visibility, single policy-based enforcement and full automation, along with trusted AI-assisted operations, should help operations teams get on top of increasing demands on the network.
I hope to see you in Barcelona at Explore, and if you have any questions please reach out.
If you would like to hear all the updates from Explore keep an eye out for our UK event on the November 22nd - https://www.uk.cdw.com/events/vmware-explore-session/

-3.png?width=1200&height=330&name=MicrosoftTeams-image%20(5)-3.png)